Introduction
The evolution of cloud computing has transformed how organizations manage IT infrastructure and security. As workloads move to the cloud, traditional approaches to securing networks, applications, and data struggle to keep pace. Legacy security models built around trusted perimeters and static configurations fail to address the complexities of modern environments, where users, devices, and applications are distributed across dynamic hybrid and multi-cloud architectures.
Zero Trust has emerged as the definitive approach to address these challenges. Unlike traditional models, which assume trust within the network perimeter, Zero Trust adheres to the principle of “never trust, always verify.” It ensures that every user, machine, and application attempting to access resources is continuously authenticated, authorized, and monitored, irrespective of their location. In this article, we explore Zero Trust’s key principles, practical implementation, and its profound impact on business operations.
What is Zero Trust and How Does it Work?
Zero Trust is a modern security framework designed to eliminate implicit trust and enforce strict verification for all entities—users, machines, and applications—before granting access. The model operates under the assumption that threats can originate from both outside and inside the network, making no distinction based on location. This paradigm is particularly suited to cloud environments, where traditional perimeter-based security is impractical and insufficient.
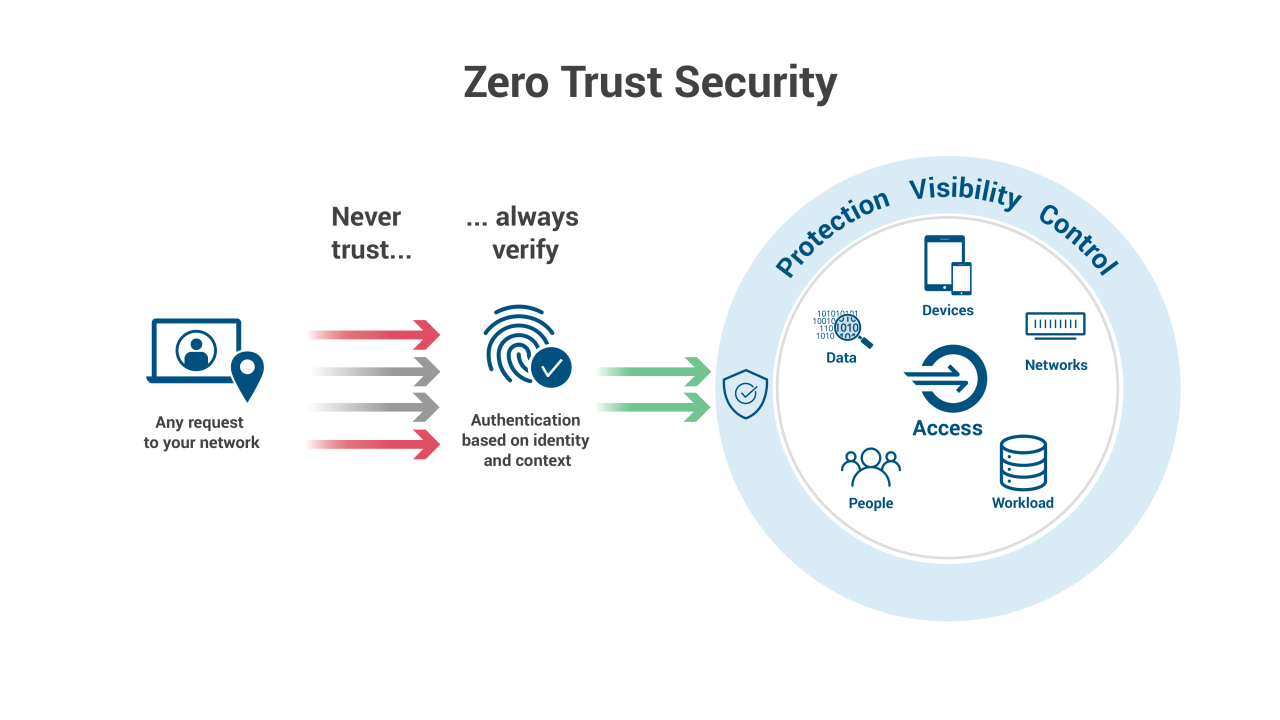
The foundation of Zero Trust lies in its core principles:
- Continuous Authentication and Authorization: Access is not granted permanently; it is continuously verified throughout a session. This ensures that access remains secure even if a user’s or machine’s context changes.
- Dynamic Policies Based on Context: Decisions are made in real-time, using contextual information.
In practical terms, Zero Trust operates by integrating multiple security technologies, including identity and access management (IAM), encryption, real-time monitoring, and automated response systems. For example, an employee logging in from an unfamiliar device outside the usual work hours may be prompted for additional verification steps. Similarly, machine-to-machine communications in the cloud are secured through mutual TLS (mTLS) and cryptographic certificates, ensuring that only authorized services interact with each other.
This model not only fortifies security but also simplifies compliance, enhances operational efficiency, and supports the scalability required for modern enterprises.
Challenges
Traditional security models rely heavily on perimeter-based defenses and static configurations. These approaches focus on securing infrastructure by granting or denying access based on IP addresses. While this method worked well in static, on-premises environments, it falters in dynamic cloud environments where resources and users are highly fluid.
Managing Access by IPs
Historically, infrastructure security relied on IP whitelisting to control access. Applications communicating with databases, users accessing services, and servers talking to each other were all secured by restricting or allowing IP-based access. However, in cloud environments, IP addresses are dynamic and frequently change. This makes managing access based on IPs operationally complex, prone to error, and insufficient for securing modern systems. A single misconfigured IP can lead to security breaches or service disruptions.
Securing Machine Connectivity
Cloud-first organizations rely heavily on machine-to-machine communication, where applications, microservices, and APIs interact to deliver services. Traditional methods for securing these connections often involve manual processes, such as ITIL-based ticketing systems. These systems are slow, inflexible, and inadequate for securing dynamic cloud environments where machine identities and policies must adapt in real-time. Without automation, scaling secure machine connectivity becomes an operational bottleneck.
Scaling Security to Meet Demand
The inefficiency of traditional methods becomes particularly evident as organizations scale. Managing tokens, passwords, and credentials for hundreds or thousands of users and machines is labor-intensive and prone to errors. Delays in provisioning or revoking access not only disrupt operations but also create vulnerabilities. For instance, expired credentials or dormant accounts can be exploited by malicious actors.
The Need for Zero Trust
Zero Trust addresses these challenges by shifting the focus from static perimeters to dynamic identity verification. It eliminates reliance on IP addresses, automates machine connectivity security, and enables real-time scaling of access policies. By adopting Zero Trust, organizations can secure their resources across hybrid and multi-cloud environments without compromising agility or scalability.
Identity and Access Management: The Core of Zero Trust
Identity and Access Management (IAM) is the backbone of Zero Trust security. At its core, Zero Trust revolves around verifying identities—both human and machine—and granting access based on dynamic, context-aware policies.
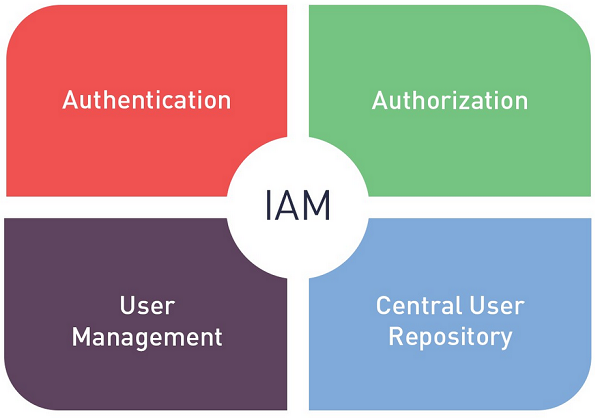
Establishing Strong Identity Verification
Zero Trust begins with the rigorous verification of every entity attempting to access a resource. For users, this often involves multi-factor authentication (MFA) or passwordless methods, such as biometric scans or hardware tokens. For machines, cryptographic certificates and service tokens are employed to establish unique identities.
Dynamic Role-Based Access Control (RBAC)
Access is granted based on roles and tasks, adhering to the principle of least privilege. This minimizes the exposure of sensitive data and systems by ensuring that users and machines only access what they need for their specific functions. Unlike static RBAC, Zero Trust incorporates dynamic context into access decisions. For example, a user accessing financial systems from a secure office network may have fewer restrictions compared to someone accessing the same system from an untrusted network.
Centralized IAM for Visibility and Control
Centralizing IAM provides organizations with comprehensive visibility into access activities across their environments. It allows for consistent enforcement of policies, streamlined audits, and enhanced compliance with regulations. By consolidating identity management under a Zero Trust model, organizations reduce the attack surface and simplify operational complexity.
The Four Pillars of Zero Trust Security
To implement Zero Trust effectively, organizations must address four core areas that encompass all aspects of secure access: machine authentication and authorization, machine-to-machine access, human authentication and authorization, and human-to-machine access.
Machine Authentication and Authorization
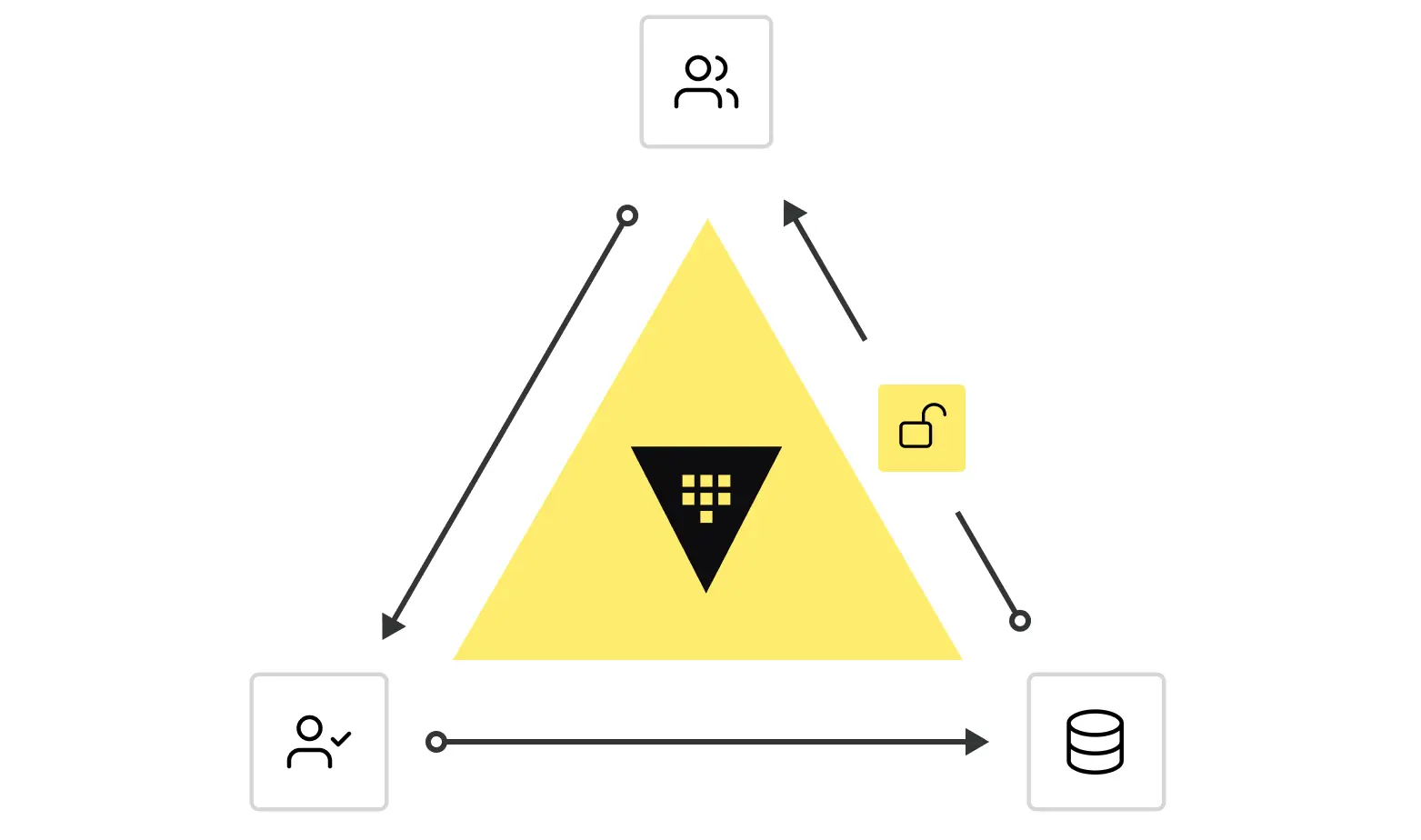
In Zero Trust, machines, just like users, require authentication and authorization to access resources. This is achieved through mechanisms such as cryptographic certificates, service tokens, and mutual TLS (mTLS). These tools ensure that only verified machines can communicate with one another. Machine identities are dynamically assigned and continuously validated, reducing the risk of unauthorized access.
For example, a microservice requesting data from a database will be authenticated and authorized in real-time, with access granted only for the duration of the interaction. By enforcing role-based access controls (RBAC) for machines, organizations can ensure that each machine has the minimum level of access necessary.
Machine-to-Machine Access
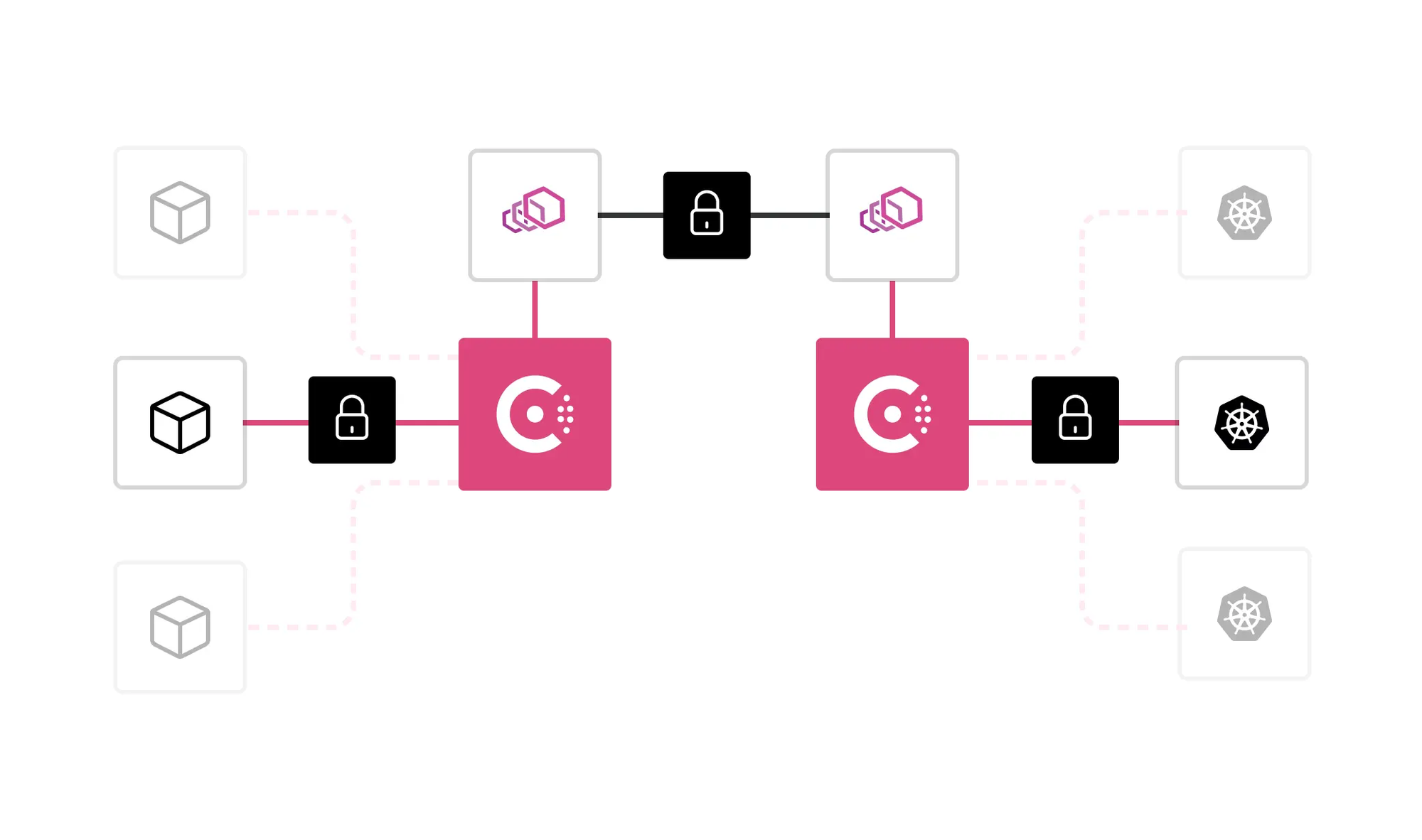
Machine-to-machine communication is integral to cloud-native environments, where APIs and microservices must interact seamlessly. Zero Trust secures these interactions by verifying machine identities and enforcing dynamic access policies. Techniques such as mutual TLS and policy-based encryption protect sensitive communications.
Consider an e-commerce platform where various services—such as inventory management, payment processing, and customer notifications—interact. Zero Trust ensures that only authorized services can access APIs and data, preventing malicious entities from infiltrating the system.
Human Authentication and Authorization
Securing human access is a critical component of Zero Trust. Users must be authenticated through strong methods like multi-factor authentication (MFA), which combines something they know (password), something they have (a hardware token), or something they are (biometrics). Additionally, Zero Trust introduces contextual policies to enhance security.
Human-to-Machine Access
Administrative access to machines and systems is another area where Zero Trust excels. Traditional methods involve static credentials, which are prone to compromise. Zero Trust replaces this with just-in-time (JIT) access provisioning, where users are granted temporary, task-specific access. Short-lived credentials and dynamic session monitoring further enhance security.
Centralized workflows for human-to-machine access provide consistent auditing and compliance. Organizations can track who accessed what resource, when, and why, ensuring accountability and enabling rapid response to potential incidents.
Benefit
Zero Trust is not just a security model; it also delivers significant business benefits by aligning security strategies with organizational goals.
Faster Cloud Adoption
One of the most tangible impacts of Zero Trust is its ability to accelerate cloud adoption. By integrating best practices and automated security controls into the deployment process, Zero Trust simplifies migrations and reduces friction. Push-button deployments enable organizations to onboard workloads securely without delays caused by manual configurations or extended approval cycles. For businesses transitioning to hybrid or multi-cloud environments, Zero Trust provides a consistent security framework that scales seamlessly across providers.
Increased Productivity
Zero Trust modernizes security operations by automating key processes, reducing the reliance on manual interventions. Centralized platforms manage user and machine access, streamlining workflows for IT teams. This allows them to focus on strategic initiatives instead of routine access management tasks. Automation also minimizes human error, a major source of security breaches, and significantly lowers operational costs. For users, frictionless access to resources enhances productivity while maintaining robust security controls.
Multi-Cloud Flexibility
As organizations increasingly adopt multi-cloud strategies, managing security across multiple providers becomes a challenge. Zero Trust offers a unified approach, enabling organizations to enforce consistent security policies regardless of the underlying cloud platform. Whether an application runs on AWS, Azure, or Google Cloud, Zero Trust ensures that access is governed by a single workflow. This flexibility allows organizations to optimize performance and cost across providers while maintaining a strong security posture.
Conclusion
Zero Trust is not merely a reaction to the limitations of traditional security; it is a proactive strategy for addressing the demands of modern IT environments. By prioritizing identity, continuous verification, and contextual access policies, Zero Trust creates a secure foundation for businesses to operate confidently in hybrid and multi-cloud landscapes.
The adoption of Zero Trust not only strengthens security but also drives business transformation. Faster cloud adoption, increased productivity, and multi-cloud flexibility empower organizations to achieve their goals while reducing risk. As the threat landscape evolves, Zero Trust provides the agility, scalability, and resilience necessary to thrive in an interconnected world. For organizations aiming to future-proof their security strategies, Zero Trust is no longer optional—it is essential.

