Introduction
In our increasingly digital world, cybersecurity is not just a luxury but a necessity. As we rely on digital assets and online infrastructures to manage information, store sensitive data, and run essential services, these systems become prime targets for cybercriminals. A successful cybersecurity strategy requires a multi-faceted approach grounded in proven principles designed to withstand modern threats. Much like the methods used to protect physical assets in ancient times, such as castles, these principles act as robust barriers, preventing unauthorized access and ensuring the integrity of critical assets.
This article delves into the five foundational principles of cybersecurity: defense in depth, least privilege, separation of duties, security by design, and simplicity, often referred to as the KISS principle. These principles, rooted in traditional concepts of layered protection and simplicity, help build and maintain a secure digital infrastructure, guarding against increasingly sophisticated attacks. Understanding and implementing each principle is essential to building a resilient cybersecurity strategy that parallels the layers of defense once used to secure castles.
Defense in Depth
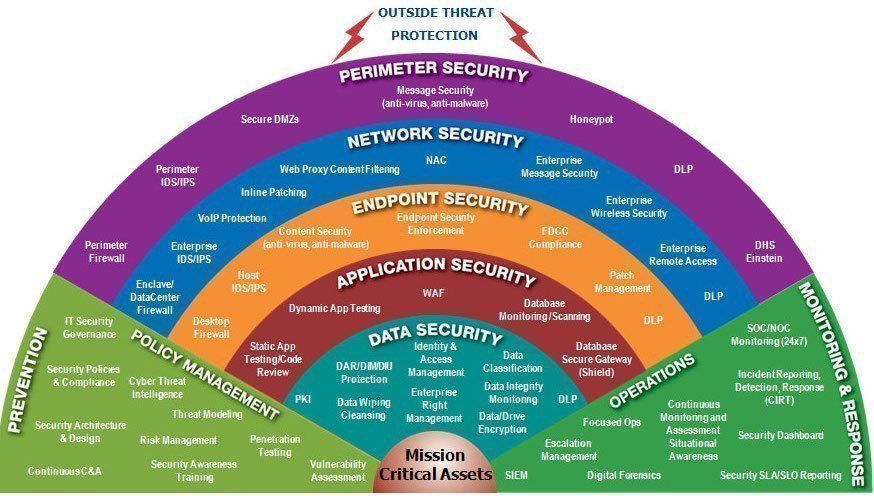
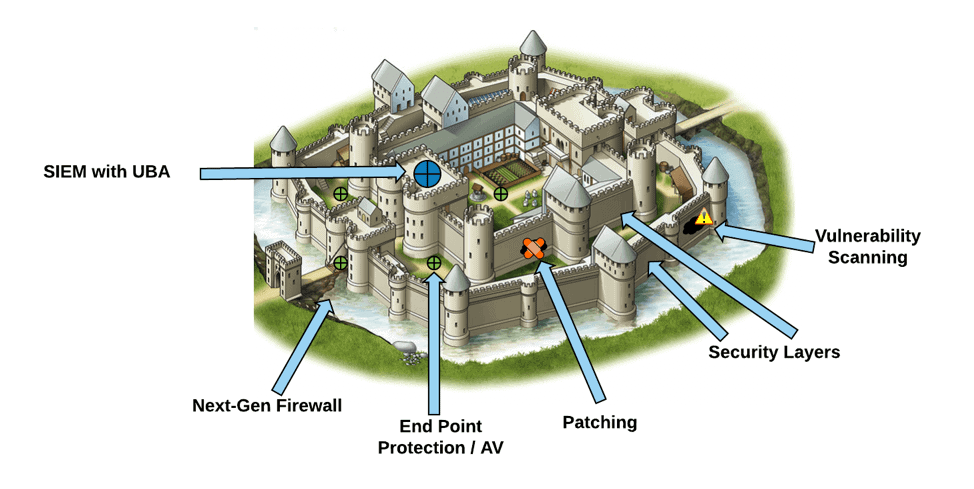
Defense in Depth is a strategy that employs multiple layers of defense to create redundancy and protect critical assets. This principle assumes that no single security measure can entirely prevent a breach, so several layers of protection must work in tandem.
Like a medieval castle with outer walls, moats, gates, and guards, Defense in Depth provides a series of hurdles an attacker must overcome to reach the core assets. In the context of a castle, defense in depth means using barriers such as high outer walls to slow down attackers, watchtowers to detect them from afar, and a drawbridge over a moat to prevent easy entry. If an attacker breaches the first layer, they face another—perhaps a fortified gate or inner wall—before they can reach the central keep. Similarly, in cybersecurity, a layered approach ensures that even if one barrier fails, others continue to protect the system.
In a digital system, Defense in Depth might involve several layers:
- Network Perimeter Security: Firewalls act as the outermost layer, regulating incoming and outgoing traffic based on predetermined security rules. Just like the outer wall of a castle, firewalls prevent unauthorized external users from entering the network.
- Intrusion Detection and Prevention Systems (IDPS): Positioned closer to the network’s core, IDPS continuously monitor traffic patterns to detect and respond to potential threats. In a castle, this is akin to having guards patrolling walls and identifying suspicious activity.
- Endpoint Protection: Each device connected to a network represents a potential entry point for attackers, much like every entrance to a castle needs to be guarded. Endpoint protection includes antivirus software, firewalls, and device management protocols to ensure that each device maintains its security posture.
- Access Controls and Authentication: Authentication serves as an inner defense layer, verifying users’ identities to ensure only legitimate personnel have access. Multi-factor authentication (MFA), for example, requires multiple pieces of evidence for user identity verification, adding an extra layer of security.
- Data Encryption: Encrypting data at rest and in transit protects it even if an attacker reaches the innermost layers. Encryption turns sensitive data into unreadable formats without the appropriate keys, much like protecting the innermost treasures in a castle’s vault.
This layered approach in cybersecurity resembles a castle’s design, providing backup defenses if one line of protection is breached. Defense in Depth is crucial because it acknowledges the inevitability of some attacks succeeding, and by employing multiple defensive measures, it minimizes the overall risk of a significant breach.
Least Privilege
The Least Privilege principle restricts users’ access rights to only the resources and permissions they need to perform their specific job functions. This minimizes the risk of both accidental and intentional misuse of sensitive information.
Imagine a medieval castle, access to important areas like the treasury, the armory, and the royal chambers was restricted to only a select few trusted individuals. Not every guard, cook, or visitor could enter these areas freely. The king or queen had their quarters, and only trusted advisors or guards had access. This arrangement ensured that critical resources and valuable items weren’t accessible to everyone inside the castle, reducing the risk of theft or sabotage by limiting the number of people who could reach sensitive areas.
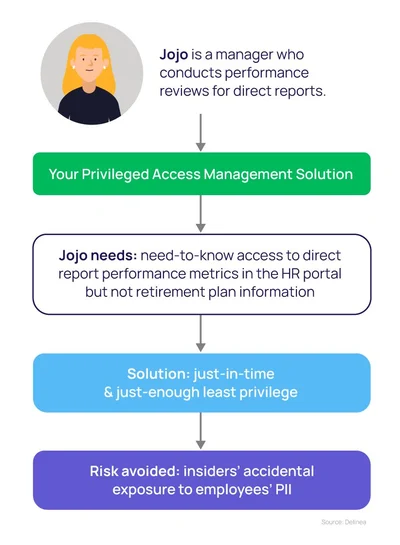
In cybersecurity, the Least Privilege principle operates similarly by limiting user permissions. Access control mechanisms ensure that users only interact with the data and systems necessary for their tasks, preventing the exposure of sensitive areas. This approach prevents unnecessary access, reduces the attack surface, and curtails potential damage in case of an account compromise. For instance, a receptionist in a healthcare organization doesn’t need access to medical records, while doctors need access to patient information but not financial records.
Implementing the Least Privilege principle involves several technical approaches:
- Role-Based Access Control (RBAC): Permissions are assigned based on job roles rather than individual identities. For example, all members of the finance team can access accounting software, but they cannot access sensitive medical records. Role-based controls reduce complexity by grouping users with similar access needs.
- Access Control Lists (ACLs): These lists specify which users or system processes can access particular resources and what operations they can perform. ACLs allow finer control, limiting specific functions on sensitive files.
- Periodic Access Reviews: Regularly reviewing access permissions helps ensure that privileges remain appropriate as job roles evolve. This is especially important in large organizations where employees often change roles.
- Just-in-Time Access: For critical tasks, users can request temporary access to sensitive systems, limiting access time to only what’s necessary for the task at hand.
By limiting access to the minimum necessary, the Least Privilege principle reduces the likelihood of insider threats and minimizes damage from compromised accounts. In a castle, this is akin to allowing only a trusted few access to the royal chambers or armory, thereby reducing the risk of betrayal or loss of valuable resources. This principle is especially important for sensitive systems and is foundational to strong cybersecurity.
Separation of Duties
Separation of Duties is a principle that divides responsibilities among multiple individuals or systems, preventing any one person or entity from having total control. This division mitigates the risk of fraud, abuse, or error. In a castle, for example, different guards and officials would manage various roles—some would oversee the treasury, others would handle the armory, and others would control access to the gates. This division ensures that no single individual holds all the power, which reduces the risk of betrayal or mismanagement.
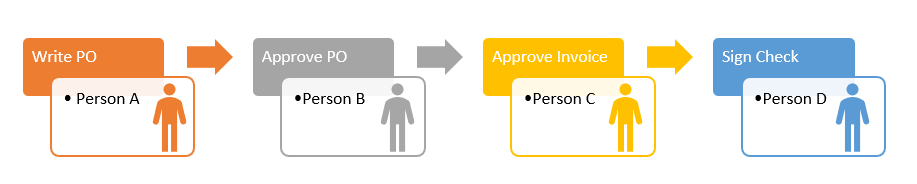
In a digital environment, Separation of Duties is crucial for systems that handle sensitive operations or confidential data. By distributing tasks among multiple individuals, organizations create checks and balances that help detect and prevent security breaches. This principle is particularly valuable in organizations with critical assets, as it makes insider threats and errors less likely to cause significant harm.
Key methods of implementing Separation of Duties include:
- Dual Control: Requiring two or more people to complete a critical task, such as authorizing a financial transaction. This approach prevents a single individual from initiating or approving significant actions, reducing fraud risk.
- Task Separation in System Administration: For instance, one team might be responsible for creating user accounts, while another manages permission settings. By separating these tasks, no single team or individual can control both access and privileges.
- Auditing and Logging: Keeping detailed records of who accesses which systems and what actions they perform. Logging provides an additional layer of oversight, as it allows organizations to trace actions back to individual users, discouraging unauthorized activity.
- Segregated Systems for Testing and Production: By separating environments for development and live production, organizations ensure that changes can be thoroughly tested before being applied to the live system. This prevents accidental or malicious disruptions.
Separation of Duties is essential in any cybersecurity strategy because it inherently limits the power any one individual or system has over sensitive operations, reducing the risk of both intentional and accidental breaches. This principle resembles how a castle would have different officials managing finances, provisions, and defense, ensuring that no single person could compromise the entire operation.
In the castle analogy, no single person could take full control over critical functions. For example, if one guard were responsible for managing both the castle gates and the treasury, the castle’s security could be easily compromised by a single betrayal or error. Instead, tasks were separated: different guards were in charge of different gates, separate officials handled treasury duties, and castle supplies were managed by specific staff. This way, each critical function had oversight and could not be managed solely by one individual.
Security by Design

Security by Design is a principle emphasizing the importance of embedding security into every stage of a system's development lifecycle rather than treating it as an afterthought. This approach parallels a well-designed castle that incorporates defensive features—thick walls, high watchtowers, and strategically placed entrances—into its structure from the ground up, rather than adding them after the building is complete. In cybersecurity, Security by Design means that security considerations are integrated into the development process, from planning to implementation, ensuring that systems are inherently resilient against threats.
Unlike traditional approaches where security measures might be added late in development, Security by Design treats security as a fundamental aspect of system architecture. By embedding security into the development process, organizations can anticipate and address vulnerabilities before they become threats, reducing the likelihood and severity of breaches. This proactive approach also ensures that security controls work harmoniously with the system rather than acting as potentially disruptive add-ons.
Key components of Security by Design include:
- Secure Coding Practices: Developers are trained to follow secure coding standards, which help prevent common vulnerabilities like SQL injection and cross-site scripting. For example, developers might use prepared statements for database queries, ensuring that inputs are sanitized and reducing the risk of SQL injection attacks.
- Threat Modeling: Threat modeling is a process where developers anticipate potential security threats and devise strategies to counter them. Much like a castle architect considering where attackers might approach and adding defenses accordingly, a development team assesses the areas where a system might be vulnerable and builds in appropriate protections.
- Regular Code Reviews and Penetration Testing: Security teams regularly review code to identify potential vulnerabilities before the system is deployed. Additionally, penetration testing simulates attacks on the system, helping to identify and address vulnerabilities early in the lifecycle.
- Least Functionality Principle: Systems should be designed to perform only essential functions, minimizing the attack surface. This principle is like a castle with only a few entry points, making it harder for intruders to find weak spots. By limiting functionality to only what’s necessary, unnecessary features that might introduce vulnerabilities are avoided.
- Use of Secure Development Frameworks: Secure frameworks and libraries that come with built-in security measures can simplify secure development. For example, using a framework with built-in data encryption and authentication protocols means developers spend less time creating security features and more time building functionality.
Security by Design is integral to creating resilient systems, as it reduces the cost and complexity of addressing vulnerabilities after deployment. A well-designed castle doesn't need constant additions to remain secure, and similarly, a system built with security at its core requires fewer reactive fixes and operates more smoothly.
Keep It Simple, Stupid (KISS)
The Keep It Simple, Stupid (KISS) principle advocates for simplicity in design, especially in security measures, to prevent errors, reduce management complexity, and enhance overall usability. Just as a castle’s layout would be designed to make it easy for defenders to quickly reach key areas, simplicity in cybersecurity ensures that systems are easy to maintain, configure, and secure. The more complex a system is, the more challenging it is to identify and fix vulnerabilities, increasing the likelihood of errors and misconfigurations.
Simplicity is especially important in cybersecurity because complex systems can be overwhelming to manage, leading to increased chances of misconfiguration and potential vulnerabilities. Additionally, users are more likely to follow security protocols if they’re simple and clear, making it easier to achieve organization-wide compliance.
Here’s how the KISS principle applies in cybersecurity:
- Standardized Processes and Configurations: Maintaining standard configurations and processes across systems makes it easier to identify anomalies. For instance, using consistent firewall rules and access policies reduces the chances of misconfiguration. It also simplifies auditing, as administrators can compare configurations across systems to detect deviations.
- Avoid Overly Complex Authentication Schemes: While robust authentication is critical, overly complicated methods (such as requiring complex, frequently changing passwords) can lead to user frustration. When security measures are too burdensome, users may seek shortcuts, such as writing down passwords or using insecure alternatives. A simplified authentication process, like multi-factor authentication with biometrics or a physical token, can provide strong security without overly complicating user access.
- Clear Documentation and Training: Simple, clear documentation and regular training ensure that employees understand and follow security protocols. Like a castle guard knowing which entrance to monitor, employees should know the security requirements relevant to their roles, which reduces errors and makes it easier to maintain consistent security practices.
- Minimalism in Features and Access: Systems should only include essential features, as excessive functionality can introduce vulnerabilities. For example, in a web application, unused APIs or services might provide entry points for attackers. By keeping the system minimalistic and free of non-essential functions, the attack surface is reduced.
- User-Friendly Interfaces: Security settings should be easy to navigate, ensuring that users and administrators can easily access and configure security features. A simple, intuitive design reduces the chance of misconfiguration, which can create vulnerabilities. Much like a castle with clearly marked pathways and gates, a well-designed interface makes security settings accessible and prevents mistakes.
The KISS principle is highly effective in reducing complexity, which in turn minimizes the potential for security gaps. Just as a straightforward castle layout enabled defenders to maintain control and respond quickly, a simple cybersecurity strategy facilitates efficient management and quicker incident response.
Application of the Principles in Real-World Cybersecurity
When applied together, these five cybersecurity principles—Defense in Depth, Least Privilege, Separation of Duties, Security by Design, and KISS—form a cohesive and resilient security strategy. Each principle contributes to a multi-layered approach that strengthens organizational defenses, just as each feature in a well-designed castle contributes to its overall security.
Consider a large organization, such as a government agency or financial institution, which manages sensitive data and critical systems. Here’s how these principles might be applied in a real-world setting:
- Defense in Depth: The organization would implement multiple layers of security, starting with perimeter defenses such as firewalls and intrusion detection systems. Internally, systems would be further protected with endpoint security, encrypted data storage, and internal firewalls. These layers ensure that even if an attacker breaches the perimeter, multiple inner defenses protect sensitive data.
- Least Privilege: Access to sensitive systems and data would be limited to employees who absolutely need it for their job functions. For instance, employees in the human resources department could access personnel records but not financial databases, while finance employees would have access only to accounting software. This reduces the risk of unauthorized access and potential insider threats.
- Separation of Duties: Responsibilities for key tasks would be divided. For example, while one team manages system updates, a separate team reviews and audits these changes. In the case of financial transactions, one employee might initiate a payment while another approves it. This approach ensures that no single person can independently make critical changes, reducing the risk of fraud and mistakes.
- Security by Design: The organization’s IT department would ensure that security protocols are integrated into the design of every new system. This means that during development, the team would employ secure coding practices, conduct regular security reviews, and test the system for vulnerabilities. For instance, all software applications would undergo vulnerability testing before going live to prevent common issues like SQL injection.
- KISS: Finally, the organization would keep its security processes and policies as simple as possible. Standardized configurations across all systems would minimize the risk of misconfiguration, and authentication methods would be streamlined to balance security with user convenience. Clear, concise documentation and training ensure that employees understand security protocols and can follow them without excessive complexity.
Interconnectedness of the Principles
While each principle serves a unique purpose, they’re interconnected and mutually reinforcing, much like the elements of a castle’s design. Defense in Depth relies on the Least Privilege principle to minimize access points; Separation of Duties complements Least Privilege by ensuring that no one person has unfettered access. Security by Design naturally aligns with the KISS principle, as systems designed with security in mind are often simpler and easier to maintain.
For example, Defense in Depth and Separation of Duties work hand in hand by creating multiple barriers across which no single individual has total control. Security by Design and KISS complement each other, as simplicity in design reduces vulnerabilities and enables Security by Design to function effectively without adding unnecessary layers of complexity.
Together, these five principles create a layered, interlocking framework for cybersecurity that protects against both external threats and internal risks. This strategic approach is akin to the defense of a well-fortified castle, where each element—from the moat to the towers to the restricted access areas—plays a vital role in protecting the occupants and their assets. By understanding and applying these principles, organizations can create a cybersecurity strategy that is both resilient and adaptive, capable of withstanding the evolving challenges of the digital world.

